Yes, you can. Download the source code for a program, build it and compute the checksum for the resulting binary file, as well as the binary file you downloaded. Compare the result, and you have mathematical proof that those files are equal if the hash signatures match, or that they aren't if the signatures don't match.
This is why you should always verify the integrity of the software you download.
Ultimately, you can always build everything from source. This is what distributions like Gentoo are all about.
But is not just the security aspect that makes open source attractive to even major companies like Microsoft. Having access to the source code means that I can tweak the software to adjust to my particular needs. Later, I could contribute those changes to the original project (also known as "upstream") so that everyone can benefit from them.
This is exactly why thousands of open source projects exist today, from prominent names like Ubuntu (and by extension, derivatives like Mint and Zorin OS) to unknown libraries that power the entire infrastructure of the internet:
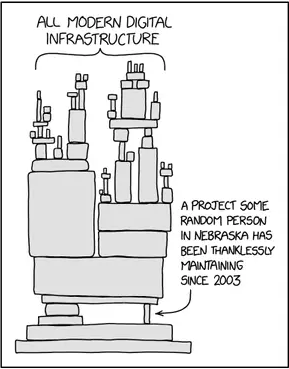
Are you referring to the XZ vulnerability? It made quite the scandal recently. See this discussion:
Yes, it's possible to embed malware in open source software just like it is in close source software. The difference is that anyone can examine the code at anytime. This doesn't make it automatically any more secure by itself, but it increases the chances of spotting these issues, which is how this vulnerability was prevented, close as it was.
One reason this XZ vulnerability did not affect Zorin OS is because of the much slower release cycle that is follows in regards to package management. This is inherited from Ubuntu and Debian, which are more focused on providing a stable and secure system, than providing cutting edge software with all the bells and whistles.
One downside of this approach is that newer software is not available quite as fast as many would like, having to go out of your way to get it. And this is where Flatpak can help.
As mentioned above by @Topaz, Flatpak has its own runtime. A runtime being a set of small programs and various libraries that other programs will make use of to run. This additional runtime will allow for packages to run independently of the system libraries that come installed with Zorin OS, and that makes it possible to have higher versions of the software than would normally be available. This brings us to:
The official repositories, no doubt. In distributions like Debian and derivatives, the packages that are included are tested thoroughly. That is by design, and a big reason why the release cycle is much slower compared to other distributions that do this differently. More time to release means more opportunities to discover stability and security issues.
Flatpak is not limited to the system libraries and thus the release cycle for each software is much faster. A developer can push an update to their software and upload it to the Flathub repository (the "store" for Flatpaks, if you will). But the cost of less time to test software as thoroughly.
In addition, not all Flatpak packages that you see are uploaded by the official developers, and is not not always verified by the Flatpak project. Those are important considerations in terms of security.
And finally, the runtime itself that Flatpak requires is software, and like all software is prone to bugs and vulnerabilities. More software installed means a bigger attack surface and more opportunities for something to go wrong.
Another aspect seldom mentioned about this runtime is that the developer needs to explicitly target a version of the runtime, in order to benefit the latest libraries and whatnot. The caveat comes when a Flatpak that depends on the Gnome runtime at version 45 gets bumped to version 46 on the newest release. The Flatpak that the user installed will not get updated and will remain at version 45. This leads to the awkward situation where one of the primary incentives of using Flatpak packages in the first place, which is to deliver the latest versions available, is completely defeated by its own design.
To properly update, the user has to explicitly uninstall and re-install that Flatpak package.
The security aspect of Flatpak comes from its design around permissions, similar to mobile apps. For example, if you download something malicious, that something may not have access to sensitive system libraries. But it can lead to a lot of awkward issues, and it often does (just browser the forum to get a sense of it), although luckily is not always difficult to work around those issues.
See more about this:
In summary, everything has pros and cons, and there's a time and place for everything. Personally, I'd recommend sticking to the official repositories as much as possible. Flatpak is an decent alternative, but not something I'd recommend as the default option as it tends to cause more headaches than it is worth. Unfortunately, the Software Store prioritizes Flatpaks over native formats.
Contrary to what most people will tell you, you don't actually need the latest and greatest versions of software all the time. When you do, you can find alternative sources such as Flatpak, or build the software from source yourself.