Not sure where to put this but cups-browsed is running on my system so I have disabled it and blocked UDP port 631 on my router. Just a heads up on OpenPrinting vulnerability.
To be clear, to exploit this you need to be specifically targeted (unlikely to happen on a personal computer over the internet) and you need to explicitly send a print job to the fake printer that a would-be attacker has setup in your system. In other words, while the vulnerability is real, it doesn't mean an automatic check mate or anything of the sort.
However, it would be better to avoid the problem from the get go by disabling the service altogether, in case you are not using a printer. You can do so by running this command on a terminal:
sudo systemctl disable --now cups
If you do use printers, Zorin OS comes with a built-in firewall that you can use to block incoming connections to port 631/UDP.
-
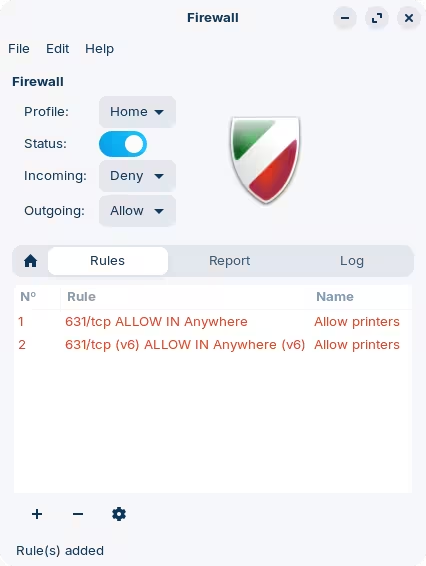
Launch Firewall Configuration from the applications menu.
-
Enable the firewall using the slide on the "Status" indicator. Once enabled, by default, it will block all incoming connections and that would already be enough to prevent this vulnerability. If you do need to allow some incoming connections, let's say from other printers in the system, you can create an Allow rule for that.
-
To add new rules click on the + sign at the bottom of the window.
-
Move to the "Simple" tab, and fill the detail as per the screenshot below:
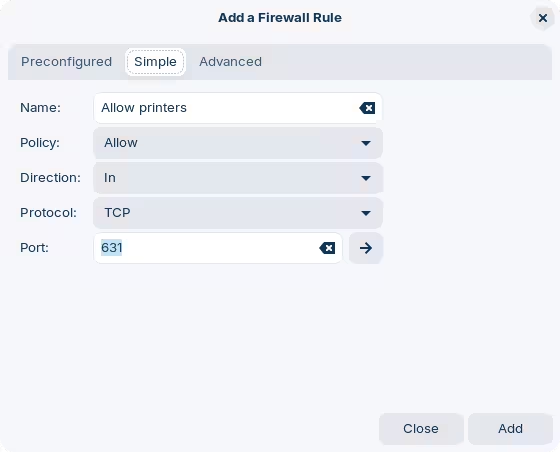
The Name is just a hint for you to remember what the rule is doing. Policy and Direction mean that we're allowing incoming traffic (as mentioned, by default every incoming connection is blocked). As for the Protocol, the vulnerability seems to apply to UDP specifically so we don't want to allow that; select TCP. The Port that CUPS uses by default is 631.
-
This should look something like this:
Keep in mind that some services may need to receive connections in order to work properly, for example things like Steam. If you do enable the firewall, you'll have to figure out what needs allowing explicitly.
Another way to work around that in a more relaxed way is to do the reverse of what just did. Change the default incoming policy to Allow and create a Block rule for port 631/UDP, instead.
I received updates today for this on pop os
Yes Zorin and Solus updated yesterday and today respectively.