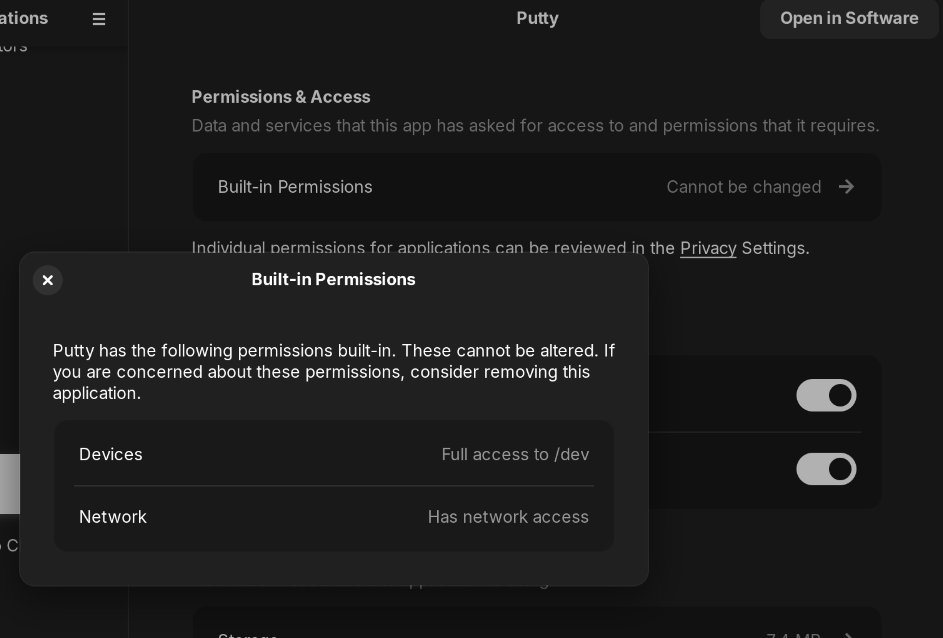
Good day everyone. Wondering if anyone else has seen this. I have a USB to serial adapter I use to tty into routers and whatnot. Because I like Putty, I downloaded the flatpak from the store. The computer sees the USB adapter as ttyUSB0, however when I run the flatpak I am told I don't have permissions to access the device. So I spent some time seeing if there was a simple way to run it as sudo only to come to the conclusion it wasn't worth the problem. So I then chmod the /dev/ttyUSB0 file to 777 and now it works. I also checked the application permissions for the flatpak and in there it states I have permissions to all devices in /dev/, however it wasn't until I did the 777 did it work. I am wondering if anyone knows if this is a problem with flatpak, the program, or possibly how flatpak is packaged with ZorinOS, and if there is a more appropriate way to solve this problem without changing permissions on core ZorinOS files.
You are mixing two phrases, flat and snap. They are two different package system. Which one did you install?
Do you remember what were the permissions before? I suspect the issue here is that flatpak packages run without privileges, and thus don't have access to read from the device.
I wouldn't say this is a bad thing per se, quite the opposite; most processes don't need this level of access. How big of a security risk this is, I'm not one to say but I'm pretty sure there's a good reason for it.
But now that you know this is a permission issue, a more "proper" solution would be to narrow down the permissions to only give the minimum required to get it to work.
For that, first you should restore permissions to the way they were before. If you don't know, I would guess they're no different than other devices and assign 640.
sudo chmod 640 /dev/ttyUSB0
Then, you can create an access control list for this particular file to grant read access to your user:
sudo setfacl -m u:zenzen:r /dev/ttyUSB0
The -m here modifies the access control list for this file and grants read permissions to the user "zenzen" – obviously, change this to your own accordingly.
You might need to log out and log back in for changes to take effect.
One big caveat to modifying permissions to device files directly is that these are prone to change as you plug and unplug devices. This means that you may run into this issue if plug more devices of this kind. It's probably not a super big deal here, I don't think that /ttyUSBx are too common, but something to keep in mind.
Thanks for the reply. This is why I bring it up here. If there is a fault, be it the one who packaged the flatpak, or perhaps within Zorin itself, I thought it should be know as it seems to me devices of this type in a consumer OS probably should 'just work' without any hoops to jump through.
The original permissions were crw-rw----. I'm assuming this is 640, did not do the translation. I'll switch it back to this and try your solution. What I don't know is if setfacl is used, is this also a change to the underlying OS, or is this done at the user level and this information stored in the users home directory? Ultimately a solution would be to put this activity into easy mode in such a way that an upgrade to the OS would not revert this configuration. I used 777 just to get the job done as I was in the need to get some work done at the time and did not want to fight the operating system.
Here are the permissions of the flatpak pulled form the store.
For what it is worth, the permissions I set to ttyUSB0 was not maintained over a disconnect/reconnect of the device for either chmod or setfacl. It reverted to the original permissions probably inherited from the directory it's in.
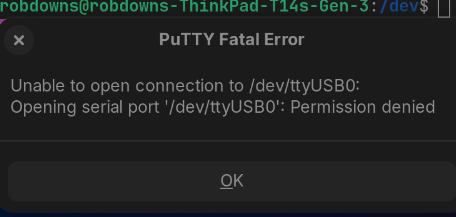
setfacl does modify the file to crw-rw----+, but does not permit the program to read the file. chmod 666 is the most restrictive permission I have found that lets the flatpak read the device, but again, it does not carry over from an unplug-replug of the device.
Have you tried flatseal?
I have now! No dice however. Had a thought and booted the laptop with the USB adapter connected at boot time, but that made no difference.
Mmm, of course, this makes perfect sense actually... should've think of it earlier ![]() Device files don't persist in the drive like regular files do, as they are created and destroyed as needed by the system. They are an abstraction created by the system in order to interact with physical hardware and other internal mechanisms – like random number generator
Device files don't persist in the drive like regular files do, as they are created and destroyed as needed by the system. They are an abstraction created by the system in order to interact with physical hardware and other internal mechanisms – like random number generator /dev/urandom.
This also answers your question as to where is this information regarding permissions stored at, partly anyway. File permissions are stored with the file itself at the file system layer. Although not every file system supports the same permission features (I can't think of any examples right now), and there are indeed additional features built on top of the kernel instead of the file system, like AppArmor.
To me, this all looks like a regular file permission issue. Many other device files need elevated privileges, and there's usually no reason to interact with them or configure anything directly. In this case, Flatpak is getting in the way because it's designed to run programs with regular user privileges. This is generally a good thing, but in this case not quite what you need.
In this particular case, I think the simplest solution that works best is to uninstall the flatpak version of putty, install the .deb version of the package, and run it with sudo putty. Although I admit that I don't know if it's possible to run flatpak packages as root.
The tricky part with the just works thing is that it can be very relative. Just as an example, I expect the system to ask for my password when attempting to install updates or edit certain configuration files. But others have complained about this very thing here in these forums, and actively worked around it out of convenience.
This is not unreasonable, but file permissions in Linux work under the "least privilege principle", meaning that regular users simply don't need direct access to device files, among many other things. So it's not that it doesn't work, it just doesn't work quite as one would expect when thinking about their own convenience. Which, again, is not an unreasonable position, but one that doesn't quite fit the security model.
As mentioned above, I think it'd be much simpler to install the regular .deb package and run as root.
Yes, there is a CLI method for this, but this is what I did to resolve the problem in a way I prefer.
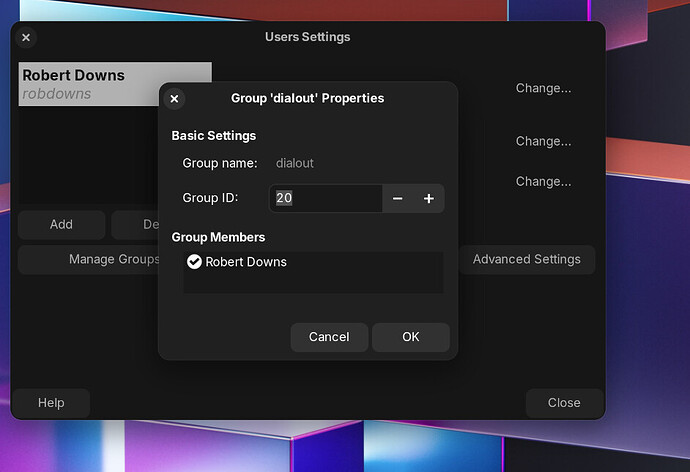
- From the cli, sudo apt install gnome-system-tools
- Open the User Settings UI from the Gnome Launcher.
- Click on Manage Groups and scroll to and select dialout.
- Click on properties and then put a check mark in the radio button for the user that needs ttyUSB permissions.
- Give permissions to make the changes when asked for your password.
- Install the Putty flatpak from the store.
- Enjoy using your software without jumping through hoops.
Perhaps Zorin could package the OS such that by default all users are made part of the dialout group, and possibly others of this nature that might make sense.
This topic was automatically closed 90 days after the last reply. New replies are no longer allowed.