I agree; it is disappointing. It's like ... "do better, guys." Ya know? Just saying ...
Excellent post. Thank you, Aravisian. Very insightful and introspective.
Also, sorry, I guess, for kinda helping make this possibly happen.
I'm done here, anyway. Back to our regular programming, folks ...
One last thing. I wouldn't mind using XFCE, but I do like my "eye candy" with the desktop environment I use. Zorin OS has that; no problem. Simple fade-ins, fade-outs, etc. Nothing fancy. Same for Linux Mint. Simple. With XFCE, there are no fade-ins, no fade-outs, etc. No basic window animations. It's interesting, because people keep saying that XFCE is a "lightweight" desktop environment. Well, I mean, think about it. What's considered "lightweight" now, given the hardware that people mostly use nowadays? Even integrated graphics have progressed to the point where they can handle simple window animations now without any issues. I think it's time for XFCE to reconsider what's "lightweight" these days. I don't know of anyone who's still using a PC from the 90's or early 00's, for instance. I have respect for what you say around here; you've earned mine and others' respect, too. Am curious as to what you think about the point I made about XFCE. Thanks.
Splinters:
Summary
My personal view is that tangents should be splintered when they reach a point that they disrupt thread flow and discourse.
Currently, this thread's topic is covered within the first opening posts. It is not readily solvable.
It can be called a Feather Thread. It has many offshoots from its primary stem from pretty early on. It is not disrupted by current commentary because of this.
But if a tangent fleshes out into a full blown discussion - it may deserve its own thread that is reflected in the title.
Lightweight: not having those bulky frills.
But you can still get them on XFCE if you want them. Compiz brings all of that. And Compiz is the original full thing, that the Gnome Extensions are tasting from.
True. We may as well discuss something more productive in the meantime ![]()
Huh. I'll have to look into Compiz on XFCE. Thanks.
You might start a new thread. ![]()
There is a new thing about it, that I do not remember off-hand... you must install a modern manager for it. So it can be a bit tricky since using an older guide can lead you astray.
It looks like this firmware update might have been getting stuck on your installation. To try and resolve this issue, please first install the latest updates from the Software Updater or by opening the Terminal (Ctrl+Alt+T) and entering these two commands:
sudo apt update
sudo apt dist-upgrade
After installing these updates, restart your computer before continuing.
Next, it should be possible to manually install this firmware update and clear the pending database afterwards – so this message shouldn't appear again – by opening the Terminal and entering these four commands:
sudo fwupdmgr refresh
sudo fwupdmgr get-updates
sudo fwupdmgr update
sudo rm /var/lib/fwupd/pending.db
Afterwards, restart the computer to apply the changes.
If this didn't resolve the issue, could you please post the text output after running the four commands (directly above) in the Terminal? If possible, please also include the text output from the following command as well:
fwupdmgr get-devices
In addition, could you please let us know if you've made some prior modification(s) to Zorin OS after installing it to your computer? These modifications may include one or more of the following:
- adding third-party software repositories to your system
- manually editing any system files
- executing unofficial scripts/commands
This information would help us to troubleshoot the issue.
Thank you, Artyom.
Thank you very much Artoym.
Thanks to Artyom for responding. However I do feel that Secure Boot has become a liability having read the flaws present, the fact that Microsoft have only fixed one cve issue and not the second, still leaving hardware vulnerable. We cannot control what Microsoft do, but I wonder if disabling secure boot and instead apply a strong Password that has to be entered before the system boots would be a better temporary solution for dual-booters until Microsoft gets its act together.
Vulnerabilities can take time to be patched - always. That is a risk we all take - including undiscovered vulnerabilities.
Secure Boot can still be beneficial to dual boot users - these vulnerabilities require direct access to the computer (though one does acknowledge a possible remote vector).
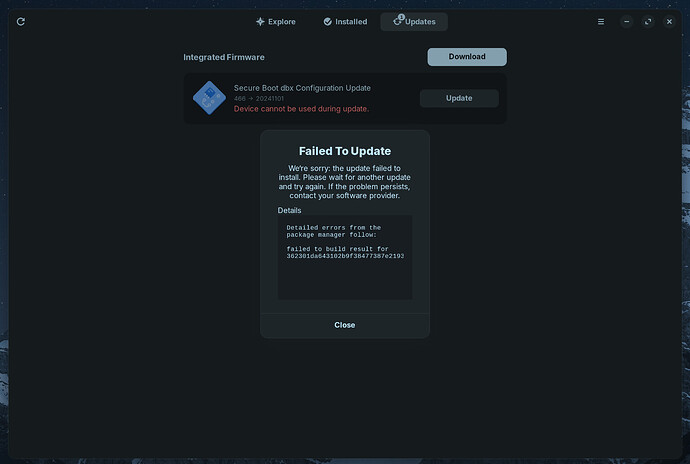
Issue not resolved. Text output below (updated).
"user@Desktop:~$ sudo fwupdmgr refresh
[sudo] password for user:
Firmware metadata last refresh: 42 minutes ago. Use --force to refresh again.
user@Desktop:~$ sudo fwupdmgr refresh --force
Updating lvfs
Downloading… [***************************************]
Successfully downloaded new metadata: 1 local device supported
user@Desktop:~$ sudo fwupdmgr get-updates
Devices with no available firmware updates:
• SDSSDA240G
• System Firmware
To Be Filled By O.E.M.
│
└─UEFI dbx:
│ Device ID: 362301da643102b9f38477387e2193e57abaa590
│ Summary: UEFI revocation database
│ Current version: 466
│ Minimum Version: 466
│ Vendor: UEFI:Linux Foundation
│ Install Duration: 1 second
│ GUIDs: c6682ade-b5ec-57c4-b687-676351208742 ← UEFI\CRT_A1117F516A32CEFCBA3F2D1ACE10A87972FD6BBE8FE0D0B996E09E65D802A503
│ f8ba2887-9411-5c36-9cee-88995bb39731 ← UEFI\CRT_A1117F516A32CEFCBA3F2D1ACE10A87972FD6BBE8FE0D0B996E09E65D802A503&ARCH_X64
│ Device Flags: • Internal device
│ • Updatable
│ • Supported on remote server
│ • Needs a reboot after installation
│ • Only version upgrades are allowed
│ • Signed Payload
│
└─Secure Boot dbx:
New version: 20241101
Remote ID: lvfs
Release ID: 108324
Summary: UEFI Secure Boot Forbidden Signature Database
Variant: x64-compat
License: Proprietary
Size: 23.3 kB
Created: 2023-05-09
Urgency: High
Vendor: Linux Foundation
Duration: 1 second
Release Flags: • Is upgrade
Description:
This updates the list of forbidden signatures (the "dbx") to the latest release from Microsoft.
An insecure version of Howyar's SysReturn software was added, due to a security vulnerability that allowed an attacker to bypass UEFI Secure Boot.
user@Desktop:~$ sudo fwupdmgr update
Devices with no available firmware updates:
• SDSSDA240G
• System Firmware
╔══════════════════════════════════════════════════════════════════════════════╗
║ Upgrade UEFI dbx from 466 to 20241101? ║
╠══════════════════════════════════════════════════════════════════════════════╣
║ This updates the list of forbidden signatures (the "dbx") to the latest ║
║ release from Microsoft. ║
║ ║
║ An insecure version of Howyar's SysReturn software was added, due to a ║
║ security vulnerability that allowed an attacker to bypass UEFI Secure Boot. ║
║ ║
║ UEFI dbx and all connected devices may not be usable while updating. ║
╚══════════════════════════════════════════════════════════════════════════════╝
Perform operation? [Y|n]: Y
Downloading… []
Decompressing… []
Decompressing… []
Authenticating… []
Authenticating… []
Restarting device… []
Writing… []
Decompressing… []
Writing… []
Restarting device… []
Waiting… [***************************************]
Successfully installed firmware
An update requires a reboot to complete. Restart now? [y|N]: N
user@Desktop:~$ sudo rm /var/lib/fwupd/pending.db
user@Desktop:~$ fwupdmgr get-devices
To Be Filled By O.E.M.
│
├─SDSSDA240G:
│ Device ID: 5dbeb140337f610d54913c0f43d15fdaa0eafb51
│ Summary: ATA drive
│ Current version: Z32070RL
│ Vendor: SanDisk (ATA:0x15B7, OUI:001b44)
│ GUIDs: 7746dc94-5008-5cad-8f22-44cc22b8cc7c
│ 09c5ce8a-75ab-5ae0-bc4c-4040a7da82fe
│ f93a32a4-d5bc-566c-afd6-345dacb9b770
│ Device Flags: • Internal device
│ • Updatable
│ • System requires external power source
│ • Needs a reboot after installation
│ • Device is usable for the duration of the update
│
└─System Firmware:
│ Device ID: a45df35ac0e948ee180fe216a5f703f32dda163f
│ Summary: UEFI ESRT device
│ Current version: 458785
│ Minimum Version: 458785
│ Vendor: To Be Filled By O.E.M. (DMI:American Megatrends Inc.)
│ Update State: Success
│ GUIDs: 7039436b-6acf-433b-86a1-368ec2ef7e1f
│ 230c8b18-8d9b-53ec-838b-6cfc0383493a
│ Device Flags: • Internal device
│ • Updatable
│ • System requires external power source
│ • Needs a reboot after installation
│ • Device is usable for the duration of the update
│
└─UEFI dbx:
Device ID: 362301da643102b9f38477387e2193e57abaa590
Summary: UEFI revocation database
Current version: 466
Minimum Version: 466
Vendor: UEFI:Linux Foundation
Install Duration: 1 second
Update State: Needs reboot
Last modified: 2025-06-17 09:36
GUIDs: c6682ade-b5ec-57c4-b687-676351208742
f8ba2887-9411-5c36-9cee-88995bb39731
Device Flags: • Internal device
• Updatable
• Supported on remote server
• Needs a reboot after installation
• Only version upgrades are allowed
• Signed Payload
user@Desktop:~$ "
You should do a Reboot.
I did/have rebooted; I just initially went 'no' to capture all of the text.
Could you please let us know if the issue still persists after restarting your computer now?
If so, could you copy & paste the error message or upload a screenshot of it here?
Could you please try running these two commands in the Terminal:
sudo fwupdmgr refresh --force
sudo rm /var/lib/fwupd/pending.db
Finally, please restart your computer once more to try and resolve this issue.
If the message still appears in the Software store after this, could you please let me know the make & model number of your computer or its motherboard (if it's a self-built PC)? This would help us to investigate the issue further.