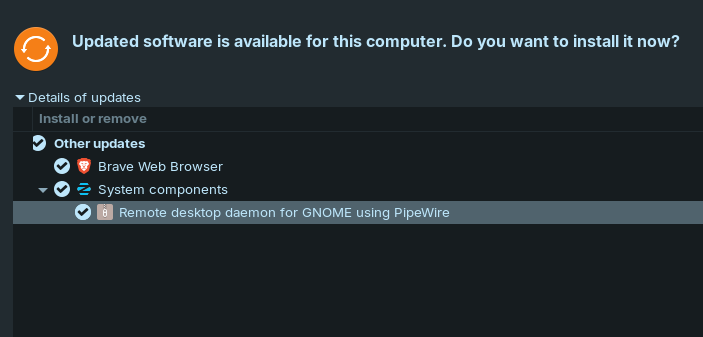
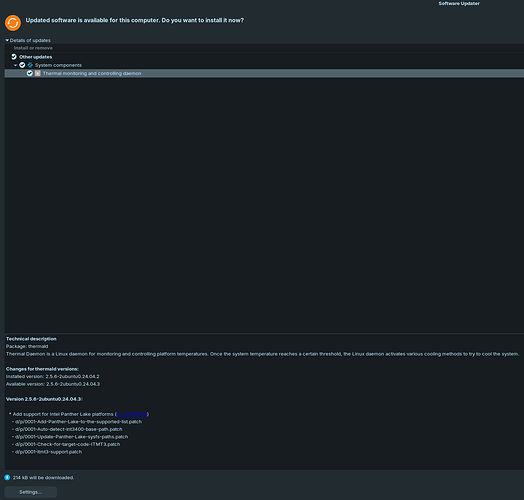
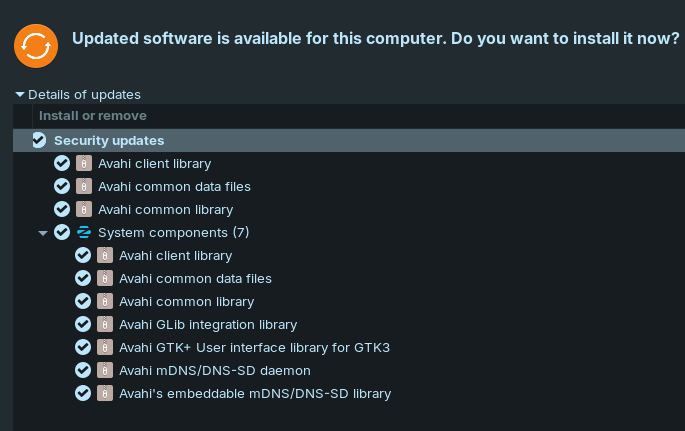
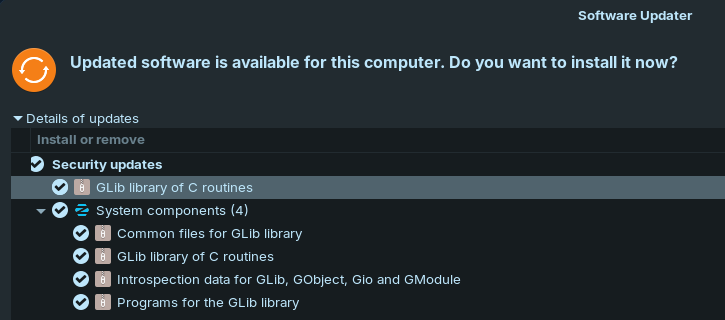
Changelogs:
For those who are interested in tracking updates but don't check their logs I thought it may be a good idea for me to combine changelogs when new updates come out and put them as forum posts (I don't work on Zorin OS just a excited user who reads changelogs)
In addition to this there was some security updates in addition to this that came out at the time of writing this however that is not as exciting.
Technical description
Package: linux-firmware
This package provides firmware used by Linux kernel drivers.
Changes for linux-firmware versions:
Installed version: 20240318.git3b128b60-0ubuntu2.21
Available version: 20240318.git3b128b60-0ubuntu2.22
Version 20240318.git3b128b60-0ubuntu2.22:
- Miscellaneous Ubuntu changes
- [Workflow] Update the gitea workflow
- [Workflow] Move checkout to top of workflow
- [SRU] Upgrade Intel xe GUC to v70.49.4 for Intel Panther Lake (LP: #2127969)
- xe: Update GUC to v70.49.4 for BMG, LNL, PTL
- Support for Realtek audio solution ALC3329B+ALC1708B on new Dell PTL platform (LP: #2129952)
- realtek: rt1321: Add patch firmware of MCU
- [SRU][R/Q/N] mt7925: Support 802.11d and CQM events for roaming (LP: #2130381)
- linux-firmware: update firmware for MT7925 WiFi device
- RTL8922A BT USB: Bluetooth: hci0: RTL: download fw command failed (-13) (LP: #2131732)
- rtl_bt: Update RTL8922A BT USB firmware to 0x41C0_C905
- Support for Cirrus Logic audio solution CS42L43 with amplifiers on new Dell PTL platform (LP: #2131725)
- cirrus: cs42l45: Add firmware for Cirrus Logic CS42L45 SDCA codec
- cirrus: cs35l57: Add firmware for a few Dell products
- Add TI tas2781 support for HP platforms (LP: #2133664)
- tas2781: Upload dsp firmware for ASUS laptop 1EB30 & 1EB31
- Add a link from TAS2XXX1EB3.bin -> ti/tas2781/TAS2XXX1EB30.bin
- ASoC: tas2781: fix the license issue for tas781 firmware
- linux-firmware: Create audio folder in ti folder, and move all the audio firmwares into it
- ASoC: tas2781: Update dsp firmware for HP and ASUS projects
- Update aic100 fw for power issues (LP: #2131936)
- qcom: Update aic100 firmware files
- qcom: Update aic100 firmware files
- Support Qualcomm RB4 graphics firmware (LP: #2133787)
- qcom: Update gpu firmwares for qcs8300 chipset
- qcom: Update A623 GMU fw
- Linux-firmware: Add qualcomm serial engine firmware qupv3fw.elf (LP: #2133923)
- qcom: add QUPv3 firmware for QCS9100 platform
- qcom: add QUPv3 firmware for QCM6490 platform
- Adjust QUPv3 driver name
- qcom: add QUPv3 firmware for QCS8300 platform
- qcom: Add QCS6490 symlink for QUPv3 firmware