Hello everyone and moderators,
So today I purchased Zorin OS 15.3 after trying the Core version on VMware Workstation Pro, I was so happy to obtain my first Linux to install it on my local laptop, but it was not smooth, the story began with my hardware specification:
- UEFI plus Secure Boot with the combination keys from ASUS and Windows.
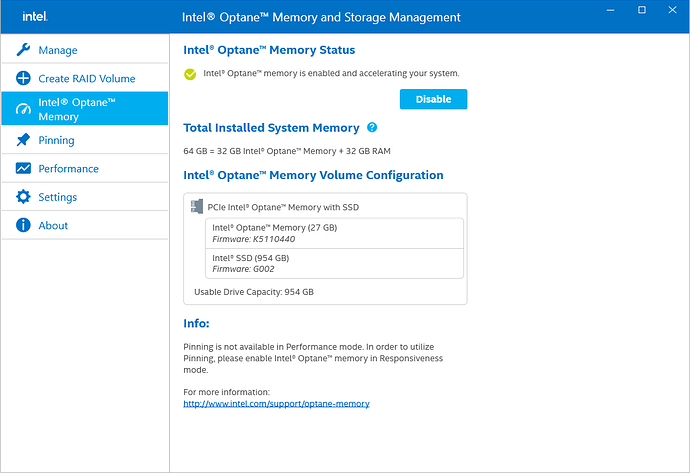
- Intel Optane with NVMe SSD H10, using Windows to manage the partition, something called "Intel Optane Memory and Storage Management", this drive has built-in Intel Optane to be configured for optimization with the SSD comes along with it, yes, it's in one package.
- NVIDIA RTX 2060.
- Intel Core i7.
- Basically, it's a ASUS Zephyrus M machine with the model number as GU502GV and I love it.
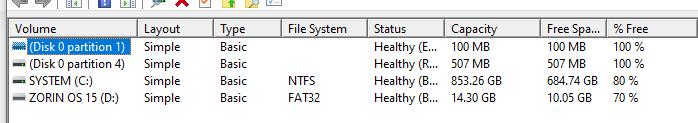
The problem started when I resized the 1TB linked Optane + SSD to get 100 GBs at the end of the partition to install Zorin OS 15.3, the installation process went well without any problem, I used the option to use modern NVIDIA drivers and connect the machine to the Internet so that it can pull updates globally during the installation. The machine needed to be rebooted so I got it rebooted without hassles, thing is, after the rebooting, the whole Boot Manager of the Windows was corrupted and the system has to repair the Boot Management and automatically restarted several times to complete the procedures.
After that, the next reboot after I went to Windows and restart it, I booted to Boot Menu of the UEFI, chose the record of the Zorin OS to try to start it up, but no luck, the screen flashed in 1 sec and returned to itself, made me to choose the Windows Boot Manager to fire things up.
So, what do we have here? I resized the partition for Zorin OS to install alongside with Windows, chose Secure Boot and put a password for it, used the modern NVIDIA drivers option to install Zorin or the SSD with Intel Optane cannot be installed with Zorin OS?
Thank you for your supports regardless it's from our beloved users or the masterminds behind!
Edited: P/S: I didn't use balenaEtcher (bE) to make the USB Boot but instead using Rufus since it could not format my thumb drive, I hate using bE