I started to read this and have been aware of glib.c issues in the past that were fixed. I couldn't see any reference as to whether this was a local attack (which means someone who has either access to the machine or on the same network), or more importantly whether the code could be executed remotely. A lot of security issues in the past have been concerned with local attacks, not remote ones. It would have been better if the research had stated what vectors enable the execution of the security breach. If someone is sat outside your house with two notebooks open you would know that they are probably trying to snarf your network!
Just found this item re Gnome.
I read with interest the second article about JavaScript. Time to switch to IceCat methinks! In terms of the cue for searching for files, I think this is off by default in Zorin (Settings) which I described in the Unofficial Manual for Zorin 15 but correct me if I am wrong. (Page 49 - Search in Settings).
Oauth fumbles yet again with more security holes:
Crosslink:
Just been reading about ESPector bootkit malware here:
and whilst looking for updated info came across this:
Go to your motherboard/computer manufacturer and check for UEFI updates:
Latest from Linux Security News:
You have to click through, to reveal which version of Thunderbird has the fixes.
See: Ubuntu 6563-1: Thunderbird vulnerabilities | LinuxSecurity.com
i.e. fixed with normal updates to Thunderbird versions
1:115.6.0+build2-0ubuntu0.22.04.1
1:115.6.0+build2-0ubuntu0.20.04.1
Bluetooth vulnerability - be sure to apply bluez patches:
Just had a critical security update come through for KDE neonuser:
" == 1.0.8-1ubuntu0.1 == * SECURITY UPDATE: denial-of-service - debian/patches/CVE-2021-35452.patch: fix check for valid PPS idx. - CVE-2021-35452 * SECURITY UPDATE: heap-buffer-overflow - debian/patches/CVE-2021-36408.patch: fix streams where SPS image size changes without refreshing PPS. - CVE-2021-36408 * SECURITY UPDATE: heap-buffer-overflow - debian/patches/CVE-2021-36409.patch: fix assertion when reading invalid scaling_list. - CVE-2021-36409 * SECURITY UPDATE: stack-buffer-overflow - debian/patches/CVE-2021-36410.patch: fix MC with HDR chroma, but SDR luma. - CVE-2021-36410 * SECURITY UPDATE: read-out-of-bounds - debian/patches/CVE-2021-36411.patch: fix reading invalid images where shdr references are NULL in part of the image. - CVE-2021-36411 * SECURITY UPDATE: heap-buffer-overflow - debian/patches/CVE-2022-1253.patch: error on out-of-range cpb_cnt_minus1. - CVE-2022-1253 * SECURITY UPDATE: stack-buffer-overflow - debian/patches/CVE-2022-43236.patch: check that image bit-depth matches SPS bit depth. - CVE-2022-43235 - CVE-2022-43236 - CVE-2022-43248 - CVE-2022-43253 * SECURITY UPDATE: stack-buffer-overflow - debian/patches/CVE-2022-43237.patch: check that image chroma format matches the SPS chroma format. - CVE-2022-43237 - CVE-2022-43243 - CVE-2022-43252 * SECURITY UPDATE: read-out-of-bounds - debian/patches/CVE-2022-43238.patch: check that image size matches sps. - CVE-2022-43238 - CVE-2022-43239 - CVE-2022-43240 - CVE-2022-43241 - CVE-2022-43242 – Fabian Toepfer fabian.toepfer@canonical.com Tue, 06 Feb 2024 16:52:09 +0100"
It looks like it doesn't affect Zorin OS.
Yes, I posted this in another thread too.
Also on Phoronix. What is interesting is clearly that systemd poses system vulnerability in sshd:
I just saw a toot (sounds really weird ![]() ) from Devuan about this as well. Now I'm more interested in learning about alternatives, it's always good to have a backup plan.
) from Devuan about this as well. Now I'm more interested in learning about alternatives, it's always good to have a backup plan.
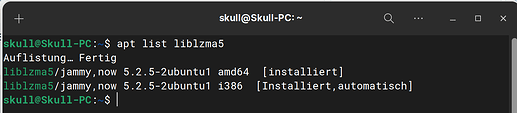
The Problem are the newest Versions 5.6.0 and 5.6.1. The Files are corrupted from the Github Repo as far as I understand that. On Zorin it is no Problem because the Version on Zorin (17) is lower:
I assume that also applies to Z16.3 editions, but not checked myself.
EDIT: 2/4/24. I have just listed it on Z16.3 Core:
![]()