I've noticed that all the folders have been accessed at about the same time and further to this that the majority of files have been accessed in the same time frame period. I don't recall seeing this before so I as suspecting malware or virus.
I would then turn the PC off for the day and when I booted next day I would see access times similar to the boot time on the folders and many files. This has now occurred for 4-5 times now.
I'm sending this post from another PC as at present I've removed internet from the suspect PC.
I will take a screen shot later (probably tomorrow) to show exactly what it is that I am seeing, but thought I'd post this first, to see if you think I'm just being paranoid !!!
Hmm.. Take a look at your router logs, if you can. Look for any connections that aren't yours.
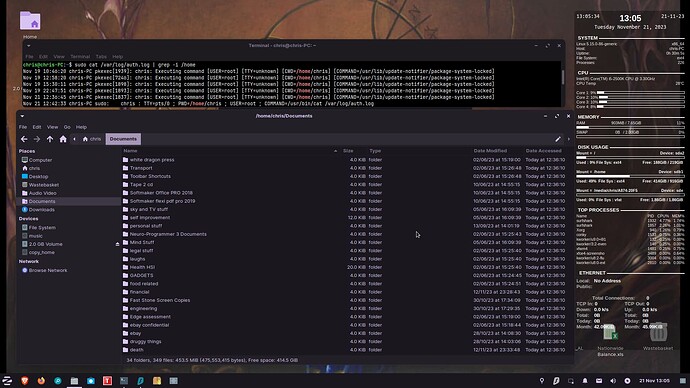
In Zorin: cat /var/log/auth.log will be lengthy, but will show you access. You can cut that down by issuing cat /var/log/auth.log | grep -i /home to see all the users that accessed files within '/home', or other locations specified like /home/user/.ssh (for SSH access / keys).
Do you have ClamTK? Definitely do some scanning with ClamAV - offline, of course..
I'm gonna look around in my notes for anything else that could pop out as an obvious attack / unauth. access...
Thanks. I will download a up to date version of clamTK on this different PC and create a live USB, I have attached a screenshot to show you the results of
I don't understand it much but it does have a suspicious "TTY=unknown" .
I booted Zorin at ~12.35 and as can be seen by the screenshot all folders can be seen to have been accessed at 1236.
I'll also try to get into the router logs from this PC and have a look at them.
Just to point out, Zorin OS Core includes Gnome Tracker, Tracker-miner-fs; these will perform standard file indexing in order to ensure that files are swiftly located and easily loaded. Disabling the tracker-miner-fs will prevent this activity. You also can safely remove tracker-miner-fs.
It may slow down file manager speeds and loading a bit.
What you are seeing may be a case of only the file indexing service - which seems likely to me given the timestamps all happening all at once.
Yes, as Aravisian said I was also thinking of simple system activity since the access time of those files and folders happens shortly after the system starts. But I still approve Chris2var's method, it's good to be so careful with malware knowing how bad they can be, if we stop having the habit of “overdoing it” with this method even after several false alarms we'll risk not doing it the day in might be really needed.
Yes, that was my initial thoughts about it, being some kind of indexing, three things changed my mind about it though.
1- Why has it just started to happen
2- This doesn't happen on two laptops with the same setup on
3- I doubt that the index tracking actually accesses / opens the files, as the only way I can change the access date/time is to actually open a file and then close it without any changes to it.
, yes being a bit paranoid pays off ....
I have some suspicions but will need to prove them first before stating them. Thanks for your comments
I'm not so certain it's about opening, more than it would just be updating the indexing.
What I would look for, especially in the router - would be IP's or IP routes that you don't recognize.
Are you:
-
Using the firewall feature within ZorinOS?
-
Using any VPN software? RiseUP VPN is free, supported by donation, but still free.
-
Using your own DNS or the DNS provided by your ISP? I absolutely recommend Cloudflare or others like AdGuard, Comodo, etc..
-
Visiting / doing / downloading things / sites / software that shouldn't be? (have to ask, almost 100% risk doing so..)
-
Using any SSH or RDP services?
-
Using a shared connection like with most apartment / condo setups?
-
Using a shared device, laptop, PC, etc. that other users have access to your machine?
Not suspecting you're causing any of this but, doesn't seem to be activity from a hacker.. as all the timestamps are all at once, seemingly. TTY=unknown would usually indicate a mistyped command, or trying to use a command that's not supported in terminal.
To check out what was accessed, use find -type f -mtime -31 for files, find -type d -mtime -31 , the -31 flag will show the last month, round-about, 31 days.
You could also look at installing chkrootkit and rootkit-hunter. They both work differently, but both work from the command line. Be aware that any changes you make to the system (install new applications, update the kernel) may provide false positives that a rootkit is present, because chkrootkit makes a note of what is running at time of its installation.
chkrootkit:
rkhunter:
I've now done scanning with clamTK, all it came up with in the /home is some pdf's that are years old and have not been looked at for years.
there was nothing at all in the /root system.
I've been through the auth.log now I understand some more about it! Nothing in the logs is of concern, looks that TTY unknown just means that it was not from a terminal. The "update notifier" isn't something to worry about either.
Aravisian ...
I'm still not sure about this having anything to do with indexing. Although I have today disabled (in the startup/application autostart menu) tracker-miner-fs and tracker-extract to see if it is that causing the accessed files and directories issue
The router logs don't show the IP's visited, or didn't as I've since changed some router settings, but I'm not putting the suspect PC back on lne at present.
In further reply to PlumpKibbles ....
Yes I am using the firewall
Yes I use surf shark VPN
I do use the DNS provided by ISP, I will change it though
no I don't visit, or download what I shouldn't be doing! I research what I want and then if I'm happy with my research then I might download something, but it's not something that I shouldn't download.
I don't know what SSH or RDP is, so I suspect that I'm not using them!
No it's not shared in anyway not the connection or the machine.
I've used
The above is for modified files/ directories, I changed this to -atime for accessed also I just done 1 day, there are many files there that I have not accessed, I will wait till tomorrow to see if disabling the gnome tracker-miner and tracker-extract do actually make a difference.
swarfendor437, thanks also as ....
I will install both chkrootkit and rootkit hunter once I'm happy that I am clear if this possible virus/ infection.
Searching for what atime definition is, I found the same thing on at least half a dozen sites, which is ....
atime stands for access time. This timestamp tells you when was the last time the file was accessed. By access, it means if you used cat, vim, less, or some other tool to read or display the content of the file.
This does tend to discount file indexing as being the cause and makes maleware seem more likely.
I'll have to look into this further ... and then come back with any more that I know or if I require any more assistance.
thanks to all who replied / assisted me so far
@Chris2var , will be interesting to know! keep us updated!
SSH is secure shell - you can remotely access machines and devices with it. You should have a ssh known hosts file in your /home directory, it'll be /home/user/.ssh/known_hosts <- check that file. If you see some devices authorized, remove them.. especially if you don't know / recognize them.
RDP is just short for remote desktop - which have some exploits out for remote access, desktop or not. Any applications you might have that allow remote desktop access, definitely give them the boot, or disable them if not using. You should be able to filter that port for blacklisting in your firewall settings as well; port 3389. But, that will block all RDP traffic - not sure if you use it at all or not.
Interested as well to see how this turns out.. very hopeful for the positive side of things! ![]() Very least, maybe just a fluke.. I haven't booted the laptop with Lite in a while, I'll have to see if I have anything like that tomorrow.. I'll edit this post when I find out.
Very least, maybe just a fluke.. I haven't booted the laptop with Lite in a while, I'll have to see if I have anything like that tomorrow.. I'll edit this post when I find out.
@PlumpKibbles , I'm not OP but i just checked my known_hosts folder & it's empty. Is that normal? or is there somewhere else to look?
Also, if we are talking about a possible device infection with Chris2var.
He needs to scan his entire RAM, temporary memory.
As the adversary/infector might be storing the payload/script only in the RAM, hiding it there.
AND whenever RAM is flushed, the infector knows the port/IP address and can detect this & simply re-infects the RAM everytime.
Also, I dont know much about encrypted malware, or if thats possible,
is it? The virus might be encrypted or obfuscated making it harder to detect.
All possibilities - called the known-unknowns. There are also known-knowns, and known-unknowns - where it's 'known' that somehow someway something could go down very soon but, how; what attack vector? Read about the 'Stuxnet' virus - that's a good one.. ![]()
The known_hosts file holds authorized SSH connections either from you or to you - this could be 'hacked' to have persistence as soon as you boot / login, rendering the threat actor a 'way in' every time you power up. Scary stuff, but you'd really really have to be a target for this to take place. And I don't suspect you have any PayPal transactions hosted through your home network lol
Any offline scanner, or bootable scanner, should be able to do that RAM scanning - pretty sure ClamAV bootable does.. RAM viruses can be easily removed - just pull the power cable, pull the ram sticks, turn it on, wait, then revert to normal - you could even ground the first and last pins on the sticks. But, RAM viruses aren't a thing that I see now, usually it's reverse TCP shelling.. Encrypted malware? Sure - I'm positive you've seen the Ransomware attacks; pretty much encrypts the drive with a note - if you pay, you get your data. If you have backups, screw the hacker - wipe the drive and get your data back ![]() just make sure your backup doesn't have the malware
just make sure your backup doesn't have the malware ![]() ..
..
If the virus is encrypted itself, it would have to have the same encryption to interact with said system - i.e.: virus and system would have to have matching hashes to interact with one another. But, encrypted or not, MITM attacks can get around that - heck, it's even known now that VPN is penetrable. You gotta be really, reeeeeaaaaalllllllyyyy wanting it though .. it ain't easy lol..
reverse TCP shelling can be done in the RAM too i think?
And would be the best strategic place to hide it?
And thanks for your insight. ![]()
I'm not positive, but wouldn't be surprised if so Just BIOS alone has gotten so robust - people have 'hacked' them to play DOOM ![]() I'm a big fan of this, as every small device I've hacked or jailbroken had to play DOOM. . was just part of the culture at the time lol and kinda difficult playing with the click-wheel on my iPod Video
I'm a big fan of this, as every small device I've hacked or jailbroken had to play DOOM. . was just part of the culture at the time lol and kinda difficult playing with the click-wheel on my iPod Video ![]() but absolutely ran!
but absolutely ran!
Hiding it: could be in a startup script, config, or within the kernel somewhere - there are tons of places that could be hidden. Or, within a JPEG or PDF .. Fun!!
"could be in a startup script, config, or within the kernel somewhere - there are tons of places that could be hidden. Or, within a JPEG or PDF .. Fun!!"
--But those are all scannable while the OS is running, which is what most people do, they have antivirus software. Whereas a RAM scan, u'd have to turn the OS off? And use an external scanner software/USB drive?
I think this is straying way beyond the OP - there are many many ways for viruses to be obtained or used; and resources on them all. It would be at such length, that this would have to be moved to a discussion post.
But, so that you're not unanswered: Yes, using a separate bootable scanner would be best. Some scanners can go as far as scanning the BIOS / UEFI along with RAM.
Is there a reason why you haven't considered a fresh install at this point? Unless you have sensitive or otherwise valuable data that you'd like to keep, I would simply re-install ZorinOS from scratch and be more vigilant for any re-occurrences.
But assuming this is not an option, you can create a separate user account from Settings -> Users -> Add User, and login to that account instead. If after a day or two of using this new user exclusively there's no indication of this misbehavior you can be sure that it's something about the original user's account.
At that point you can copy over all your data to the new user's home directory and wait for another day or two to make sure the issue doesn't happen even after this. If not, your files are good and you should be able to copy them to an external drive or computer.
@PlumpKibbles
I don't have a /home/chris/. ssh folder at all. I've done a folder search for. ssh and ssh and file search for known_hosts nothing comes up.
I don't have and remote desktop use so I've now added a block rule to firewall for port 3389.
@zenzen
I do have sensitive info /files / documents, so it makes this disconcerting, they are backed up though.
Now I need to start changing passwords etc but I need to be wary of that, so will do so on a new tablet that is only connected to mobile data and avoid using my sky router.
I have now created a new account put dummy files into it and will see how it goes as you say for a few days.
@Jessie
There is so much that can be hacked now, I've decided on a new approach, once this issue /issues are sorted out. I'm going to have all sensitive data split between the pc/ electronic storage and real physical book. That way they would only get half the information, which would be worthless without the physical book.
Thank you all, for your help so far